Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and...
42 KB (5,183 words) - 18:30, 6 June 2024
enable trusted computing features in computers and mobile devices. Related efforts involved Trusted Network Connect, to bring trusted computing to network...
6 KB (595 words) - 00:38, 12 November 2023
secure upgrades of the trusted computing base poses bootstrap problems of its own. As stated above, trust in the trusted computing base is required to make...
12 KB (1,632 words) - 01:15, 29 March 2023
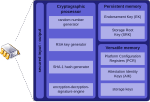
against firmware attacks. Trusted Platform Module (TPM) was conceived by a computer industry consortium called Trusted Computing Group (TCG). It evolved...
79 KB (6,479 words) - 23:40, 8 June 2024
The Next-Generation Secure Computing Base (NGSCB; codenamed Palladium and also known as Trusted Windows) is a software architecture designed by Microsoft...
79 KB (7,341 words) - 02:49, 30 May 2024
secure multi-party computation, and Trusted Computing. Confidential computing is promoted by the Confidential Computing Consortium (CCC) industry group,...
45 KB (4,300 words) - 14:31, 16 February 2024
authentic operating system starts in a trusted environment, which can then be considered trusted. Provision of a trusted operating system with additional security...
12 KB (1,536 words) - 04:24, 30 August 2023
In computing, a trusted client is a device or program controlled by the user of a service, but with restrictions designed to prevent its use in ways not...
3 KB (320 words) - 01:47, 17 October 2022
trusted system is one that is relied upon to a specified extent to enforce a specified security policy. This is equivalent to saying that a trusted system...
17 KB (2,358 words) - 22:49, 30 July 2023
The term Trustworthy Computing (TwC) has been applied to computing systems that are inherently secure, available, and reliable. It is particularly associated...
9 KB (752 words) - 13:25, 5 May 2024